The Lynx Ransomware group has been increasingly active, employing sophisticated social engineering techniques and exploiting various vulnerabilities to conduct ransomware attacks on large organisations. Their TTPs include impersonation of IT staff and the abuse of legitimate tools to gain unauthorised access, culminating in data encryption and exfiltration. This post presents a technical analysis of a newly identified Lynx ransomware binary and outlines mitigation strategies.
Key Points
- Lynx Ransomware group targets large organisations using social engineering tactics.
- They have been linked to recent data exfiltration incidents.
- The group exploits known vulnerabilities to gain access to systems.
- Organisations are urged to implement stronger security protocols and employee training.
- The ongoing threat from Lynx underscores the need for proactive cyber security measures.
Sample Overview
During an incident response engagement, CybaVerse identified a binary named 1.exe linked to the Lynx group.
- SHA256: 6e65483764d7c25523a5bbef5be99eb42349eef39d5517c46b3a4af262a80ceb
Upon dynamic analysis, its process tree includes:
- conhost.exe: Console host process.
- FXSSVC.exe: Windows Fax Service.
- ONENOTE.EXE: Microsoft OneNote, launched with an XPS document.
- OfficeC2RClient.exe: Office Click-to-Run Client, spawned with error parameters.
- onenoteim.exe: OneNote for Windows 10.
Core Ransomware Behaviours
File Encryption
The malware systematically encrypts files, appending a .lynx extension (e.g., C:\Users\user\Documents\file1.docx.lynx). It generates numerous high-entropy files (entropy ~7.99), a hallmark of encryption, and targets system drives and user directories. It also checks for available drives, possibly to infect removable media and deletes Volume Shadow Copies to hinder recovery.
Ransom Note Deployment
A ransom note, README.txt, is deployed across directories such as:
- C:\Users\user\Desktop
- C:\ProgramData
- C:\PerfLogs
The note attributes the attack to the "Lynx Group" and lists Tor onion addresses for payment negotiation:
- hxxp://lynxchatly4zludmhmi75jrwhycnoqvkxb4prohxmyzf4euf5gjxroad[.]onion/login
- hxxp://lynxchatfw4rgsclp4567i4llkqjr2kltaumwwobxdik3qa2oorrknad[.]onion/login
- hxxp://lynxchatohmppv6au67lloc2vs6chy7nya7dsu2hhs55mcjxp2joglad[.]onion/login
Victims are given seven days to comply.
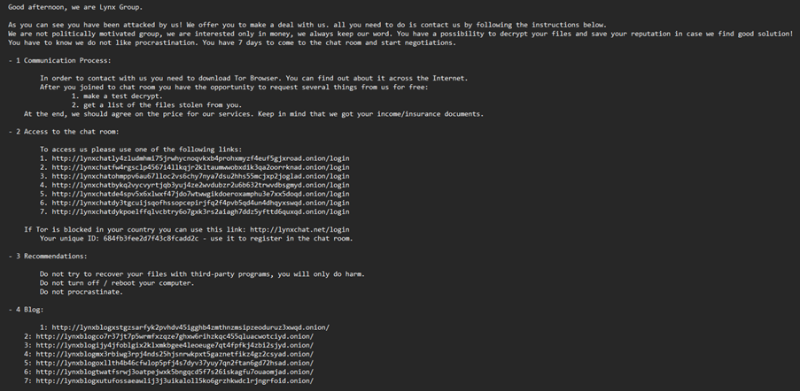
Ransom note, README.txt
System Modifications
The malware alters the desktop wallpaper by setting HKEY_CURRENT_USER\Control Panel\Desktop\Wallpaper to C:\Users\user\AppData\Local\Temp\background-image.jpg, displaying a ransom message.
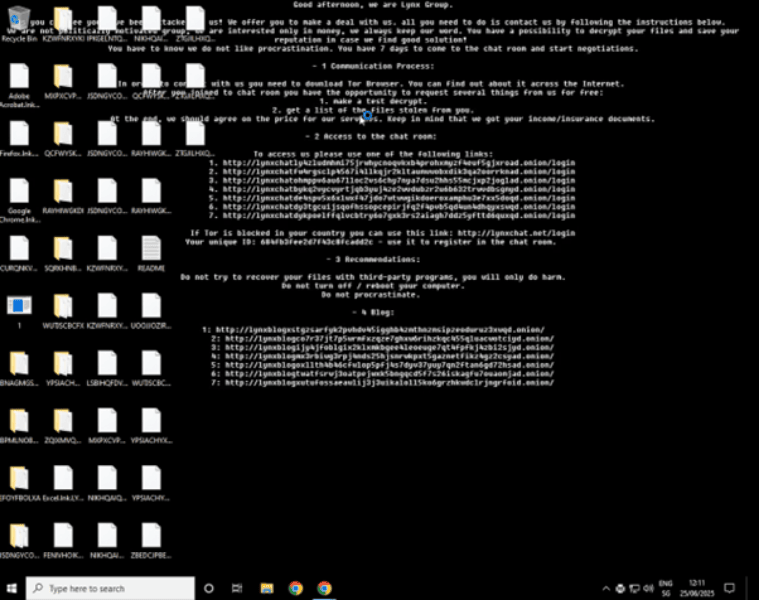
Ransom note displayed as desktop wallpaper
It also creates icon files (e.g., folder.ico, pictures.ico) in C:\ProgramData\Microsoft\Device Stage\Task\{07deb856-fc6e-4fb9-8add-d8f2cf8722c9}\, possibly to modify folder appearances and enhance visibility of the infection.
OneNote Interaction and Potential Exploit
One notable technique is the malware’s launch of ONENOTE.EXE with the command:
/insertdoc "C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\{540D88F3-8A93-4D49-BAE3-48CD9A1ACD8D}.xps" 133953414633960000
This instructs OneNote to process an XPS document from the browser cache.
Subsequently, OfficeC2RClient.exe is spawned with:
OfficeC2RClient.exe /error PID=10800 ProcessName="Microsoft OneNote" UIType=3 ErrorSource=0x8b10082a ErrorCode=0x800c0006 ShowUI=1
The error code 0x800c0006 indicates a processing failure.
Network Activity
Beyond Tor addresses as mentioned above, the malware triggers DNS queries to ecs-office.s-0005.dual-s-msedge.net (resolving to 52.123.129.14 and 52.123.128.14), likely incidental Office telemetry rather than command-and-control traffic.
No command-and-control activity was observed.
Additional Observations
- Registry Activity: Extensive modifications and queries, including wallpaper changes and system info gathering.
- Mutexes: Created to ensure single-instance execution or mark infection.
- File Operations: Opens, reads, and writes files extensively, aligning with encryption tasks.
MITRE ATT&CK Techniques
The report maps behaviours to:
- T1486: Data Encrypted for Impact.
- T1491.001: Internal Defacement (wallpaper change).
- T1566: Phishing (possibly initial access, though context suggests post-infection use).
- T1090.003: Multi-Stage Channels (Tor usage).
Conclusion
The Lynx ransomware variant demonstrates a calculated, multi-stage attack chain leveraging legitimate tools such as Microsoft OneNote, custom encryption logic, and aggressive system modification to maximise impact and reduce recovery options. Its integration of high-entropy encryption, shadow copy deletion, and Tor-based negotiation portals aligns with tactics seen in mature RaaS operations.
Recommendations
- Block outbound Tor traffic.
- Block the SHA256 hash.
- Due to evidence of a newly compiled binary, it is clear that further new, unknown, hashes will be used.
- Monitor for OneNote or XPS file activity in unusual contexts.
- Monitor for wallpaper changes to background-image.jpg in the user's temporary directory.
- Security Awareness training should emphasise IT impersonation and phishing, as Lynx’s campaigns rely heavily on social engineering.